Mobile payment security vulnerabilities: think they’re just a tech myth? Think again. You tap, you pay, and off you go. But where does your money really go? Every tap could put your financial peace in mind at risk. I’m here to peel back the curtain on the hidden dangers that you carry in your pocket – your digital wallet. From the ease of tap-and-go to the real deal on app security, we’re digging deep without sugar-coating the facts. Is your wallet safe, or is it a gateway to digital pickpockets? It’s time to secure your tap so that your savings don’t slip away. Let’s confront these threats together and stay one step ahead of the scammers.
Understanding the Risk Landscape of Mobile Payments
The Evolving Threats in Contactless Transactions
Contactless payments are quick and simple. But they have hidden risks. Thieves can tap into NFC payment vulnerabilities. They can steal your info when you tap to pay. This is because contactless cards and phones share data with the reader. If not secure, your data is up for grabs.
Digital Wallets and NFC: Convenience vs. Security
Your phone can act as your wallet. Digital wallet security is key to keep your money safe. NFC, or near-field communication, lets you pay with a tap. But when it’s easy for you, it’s easy for hackers too. They look for encryption flaws in mobile payments. This can lead to financial data theft mobile. They may even create and use insecure mobile payment apps to trick you.
Also, QR code payment fraud is a thing. You scan to pay, but what if the code is bad? Then hackers might get your card details. This kind of mobile payment hacking incident is more common than you’d think.
Biometric and two-factor authentication help. But they’re not perfect. There are issues and weaknesses here too. Hackers get smarter every day.
Smartphones carry your personal details. So, smartphone payment breaches can be huge. Thieves can get a lot of your info all at once. They use mobile pay malware to sneak into your phone. This way they can mess up your mobile transactions.
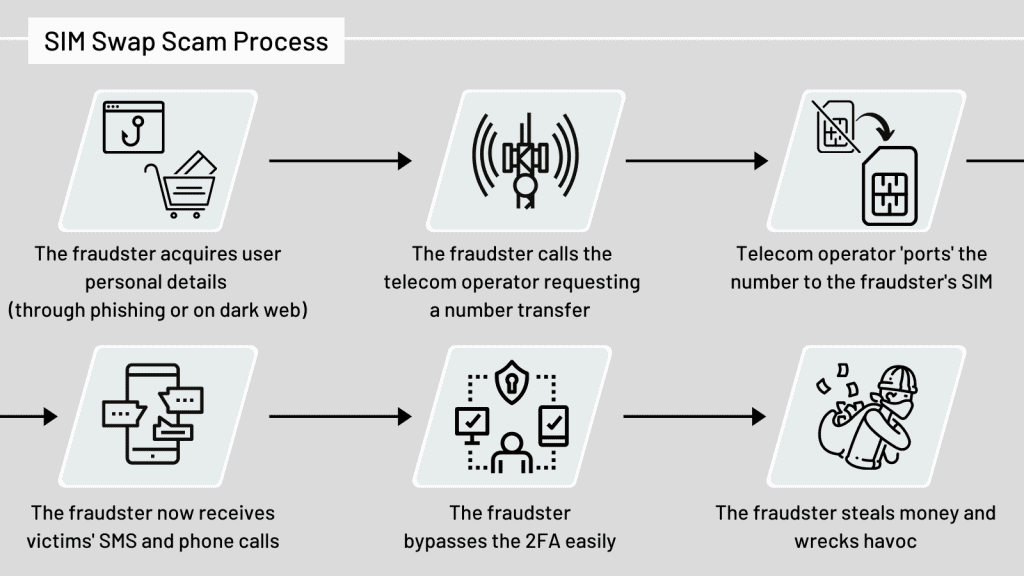
They even try stuff like SIM swap scam. They trick your phone carrier and get your number. They get your texts and calls, and yes, your payment codes.
When you shop online, you may hear about card-not-present fraud. This happens when someone uses your details, but they don’t have your actual card. Online, they don’t need it.
For peer-to-peer, or P2P payment app vulnerabilities, that’s another story. It’s easy money for thieves. They can trick you into sending money or steal your login.
Wireless pickpocketing is sneaky. Hackers can take your card info without touching you. They use gadgets to grab your data out of the air. And with Bluetooth payment data leaks, they can do it from far.
Tokenization in mobile payments is good news here. It hides your real card details when you pay. This means hackers get useless info. Third-party payment processor risks get lower with this.
Remember, apps need to be safe too. App store security measures try to block rogue apps and fake wallets. But they don’t catch all. Public Wi-Fi mobile payment dangers are real too. Free Wi-Fi is great, until a hacker watches your payment go through.
Mobile pay cyberattack trends keep changing. But so do payment data encryption standards. We get better at blocking them.
Keep your phone’s OS up to date! Outdated OS payment security is like an open door for thieves. They love it when you don’t update.
To stay safe, it’s about balance. Enjoy the tech. Just be smart about mobile payment risks.
Recognizing and Addressing Mobile Payment Vulnerabilities
Biometric and Two-Factor Authentication: Not a Silver Bullet
You trust your smartphone to pay for coffee, right? But is it safe? Let’s dive in. Biometric and two-factor authentication sound solid. They check who you are in two ways. Maybe with a fingerprint and a passcode. But here’s the thing: they’re not fail-proof. Crooks find ways around them. Think about masks that trick fingerprint sensors. That’s a biometric authentication issue. Or maybe you get a text with a code, and a hacker swipes it. That’s a two-factor authentication weakness.
How Payment Gateways Become Targets for Cybercriminals
Now, let’s talk about payment gateways. These are like bridges between you and the store’s bank. When you tap to pay, your payment info crosses this bridge. But cybercriminals target these spots. They aim to sneak in and grab your card number. Encryption helps cover your data, making it hard to grab. But sometimes, there are encryption flaws in mobile payments. That’s like having a crack in the bridge. And that’s where thieves slip in.
So, thieves use mobile pay malware to infect your phone. Then they can see your data, like a pinhole in your pocket. And with NFC payment vulnerabilities, they can get close and snatch info while you’re unaware. Simply, tapping to pay is handy but opens you up to contactless payment threats.
We also can’t forget about mobile payment risks that come from QR code payment fraud. You scan a code thinking it’s for payment, but boom, it’s a trap that can lead to financial data theft mobile-style. And these insecure mobile payment apps? They may not guard you well enough, letting hackers waltz in.
Then there’s the SIM swap scam. That’s when a bad guy pretends to be you and gets your phone number transferred to their SIM card. With that, they can mess with anything linked to your number, including payment apps. Creepy, right?
So yes, your digital wallet is at risk. You have to keep an eye out. Know about these mobile payment hacking incidents. Don’t let your guard down with smartphone payment breaches. Learn about the mobile transaction exploitation that’s out there. This way, you can tell if something’s wrong. Keep your eyes peeled, for example, when there’s news about third-party payment processor risks.
Watch out for warnings about mobile banking Trojan threat, too. That’s a sneaky virus pretending to be a legit app. Before you know it, it can slip into your phone and steal your cash. And always double-check that app before you download. Rogue apps and fake wallets want to trick you into a quick click.
Last point: Don’t do your payments over public Wi-Fi. Public Wi-Fi mobile payment dangers are too great. It’s like shouting your card number in a crowded place. Someone bad might hear it. The same goes for Bluetooth payment data leaks. It’s like leaving your wallet open, where sneaky hands can reach.
In short, mobile payment security isn’t perfect. But now, you’re wiser about the traps and how to dodge them. Stay alert, and your wallet stays safer!
Preventing Mobile Payment Fraud and Cyber Threats
Strategies to Thwart P2P Payment App Exploits and SIM Swap Scams
I’ve seen a lot. P2P apps make sending cash easy. But with ease comes risk. Hackers love easy targets. They use tricks like SIM swap scams. This is where they pretend to be you and steal your phone number. With your number, they can break into your apps. That includes your money apps. It’s scary, but I’ll teach you how to fight back.
First, protect your phone like a treasure. Use a tough password. Don’t share it. Watch for signs of a swap. Your service might cut out for no reason. If that happens, call your company fast. Be aware. If you get weird texts asking for codes or passwords, that’s a red light. Someone might be trying to get into your account.
Next, look at your app’s settings. Turn on alerts for money moves. That way, if someone tries to be sneaky, you get a heads up. Keep your app updated. Old versions can have holes that crooks can wiggle through.
Use security features within the app. Some have more than just a password. There’s stuff like fingerprint checks or face scans. These are safer. No two people have the same prints or face. Side note – even these can have issues. But right now, they’re one of the best bets.
Lastly, if something feels off, trust your gut. Call your app’s support team. Stay safe out there.
The Role of Encryption and Tokenization in Protecting Transactions
Your data needs to stay your data. That’s where encryption and tokenization jump in. They’re like secret codes for your info. Encryption scrambles your card details. Think of it like a puzzle. Only the right key can put the pieces back together. That key? It’s not easy to get. This keeps your money info safer when you buy things.
Tokenization takes it a step further. Your real card number turns into a random number. So, even if bad guys grab this number, it’s useless to them. It’s a way to pay without risking your real card details.
You can find these security tools in most digital wallets. These wallets use both encryption and tokenization. This means they’re tough for thieves to crack. Each time you tap to pay with your phone, a token acts like your card. You get to keep your actual card number a secret.
When you pick a mobile payment app, make sure it has these security tools. They’re key to keeping your money data safe. Without them, you’re waving your card info around for anyone to grab. And that’s just asking for trouble.
Remember, staying safe with tech is a lot like playing a sport. You need good defense moves. Encryption and tokenization? They’re your all-star defenders. Keep them in your team, and you’re doing a great job protecting your money.
Best Practices to Enhance Mobile Payment Security
Navigating the Dangers of Public Networks and Clickjacking
When you pay with your phone, you trust it with your money. But crooks are always looking for a way to get at it. One trick is to fool you on public Wi-Fi. They can watch what you do and grab your private details when you’re not looking. They set up fake Wi-Fi spots, and once you connect, they can see every move you make.
To stay safe, only use Wi-Fi you trust. Make sure it’s the real deal. Worried? Just use your phone’s data when you’re out. It’s harder for bad guys to mess with that.
We can’t forget about clickjacking. It’s when you think you’re clicking on something safe, but it’s really a trick. It hides the bad stuff under what looks like normal web pages. You think you’re paying for that cool new game, but you could be giving your passcodes or cash to a scammer.
Always keep an eye out for signs that something’s not right. Look for web addresses that don’t match the store’s. And if things seem off, get out of there!
Ensuring App Integrity and OS Security Updates to Combat Malware
Now, let’s talk about mobile malware. It’s like a bug that gets in your phone and does sneaky stuff without you knowing. Thieves use it to break into your phone and steal important info. They get in through apps that look okay but are really bad. This is why we must check if an app is real before we download it. It’s like making sure you know who you’re letting in the door.
We all love free apps, but check who made it and read what other people say about it. If it looks fishy, don’t take the bait. Think of it as making your phone’s lock just a bit stronger.
And what about your phone’s brain, the operating system (OS)? Sometimes, it gets old and doesn’t know how to fight new tricks. This is where updates help. They teach your phone the new moves it needs to block the bad guys.
Your phone will tell you when it’s time to learn something new, so always say yes to updates. It’s like giving your phone a shield to block the arrows that crooks fire your way. And it’s easy. Usually, it’s just a tap away.
By being smart about using Wi-Fi, checking apps and getting updates, you’re building a fort for your money. It’s all about knowing the traps and sidestepping them. Stay one step ahead, and keep your money safe.
In this post, we looked at dangers of paying with your phone and how to stay safe. We learned that even with no-touch pay and digital wallets, risks are still out there. Sure, using your face or fingerprint can help, but they’re not perfect. Bad guys often aim for payment apps, so we need to be careful.
We also talked about ways to keep mobile pay fraud at bay, like being smart about scams and using clever tech to hide our card details. And let’s not forget about doing the basics right, like steering clear of shady Wi-Fi and keeping our phone’s defenses up to date.
Remember, keeping your money safe when you tap to pay is all about knowing the tricks and staying ahead. Be smart, follow these tips, and you can tap with trust!
Q&A :
What are the common vulnerabilities in mobile payment systems?
Mobile payment systems are increasingly popular but can expose users to several vulnerabilities. Some of the common security risks include weak authentication procedures, unencrypted data transmission, malware or spyware, outdated or unpatched software, and the risk of lost or stolen devices which can give attackers access to mobile payment applications.
How can consumers protect themselves from mobile payment security threats?
Consumers can mitigate the risks of mobile payment security threats by taking several measures. These include using strong, unique passwords or biometric authentication, ensuring their devices and payment apps are regularly updated, avoiding public Wi-Fi for transactions, monitoring bank statements for unauthorized charges, and using reputable mobile payment services with robust security protocols.
What is the role of encryption in securing mobile payments?
Encryption plays a crucial role in securing mobile payments by scrambling sensitive information such as credit card numbers and personal details during transmission. This makes it extremely difficult for hackers to intercept and decipher the data. Reputable mobile payment apps typically use strong encryption methods, such as SSL or AES, to protect user information both in transit and at rest.
Are there any regulatory standards for mobile payment security?
There are regulatory standards in place for mobile payment security designed to protect consumers and ensure secure transactions. The Payment Card Industry Data Security Standard (PCI DSS) applies to all entities that store, process, or transmit cardholder data. Moreover, various regions may have additional regulations, such as the GDPR in Europe, that govern mobile payment security and data protection.
What makes NFC and RFID technologies vulnerable in mobile payments?
NFC (Near Field Communication) and RFID (Radio Frequency Identification) technologies are vulnerable in mobile payments due to potential eavesdropping, data corruption, and interception risks. These technologies allow for contactless payments but can be susceptible if not properly secured, allowing attackers to capture information from a distance or create unauthorized transactions. Robust encryption and secure channels are necessary to safeguard these types of mobile payments.